4 Common Problems with L2TP/Ipsec and How to Fix Them

March 16, 2020 started out as normal at the office.
About an hour into the day, an announcement came that the office was closing immediately due to the COVID-19 threat. All personnel were instructed to work remotely from home. Initially, the directors, who had very little time to prepare, gave out some bad information such as "you will be taking your work computer home with you." That was quickly extinguished because it was impossible. Because we couldn't take hardware home, the only solution available was to have the entire office utilize VPN technology to remote desktop into their machines. Once a remote desktop connection was available, we were to perform our work functions to the best of our abilities.
We already had a VPN server set up on a Windows Server 2012 machine. It was using the PPTP tunnel protocol. This VPN connection was sparingly used. There were a couple of non-IT users who occasionally remoted into their machine to perform some tasks most of the time because they were at a conference. The IT department had a lot more experience using VPN due to the nature of the work.
The first task was to get a large number of users who never used VPN, or remote desktop technology, connected on their home computers. After about a week of troubleshooting, most of the office had set up VPN connections on their home computers. A server that previously had two to three connections at the most now had user counts of 35 to 40 on a regular basis. We found out quickly that we were ill-prepared for such a user base and that our PPTP tunnel was not very secure.
Here's a list of the most challenging problems we encountered after the rollout — and how you can avoid them in the future.
Problem No. 1: No support for PPTP
We found that some operating systems did not support the PPTP tunnel that our server was using. Several users had MacBooks that ran on a MacOS Sierra operating system. After some research, we found that Apple had dropped support for the PPTP tunnel on the newer versions of their Operating Systems due to security concerns.
Solution: Use the L2TP/IPsec tunnel instead of PPTP
While researching the MacOS problem, we requested the help of the security team that handles our uplink. They gave us an emphatic suggestion "Stop using PPTP as soon as possible. The L2TP/IPsec tunnel is fairly simple to set up and it is far more secure."
We found many articles that discussed the issues with PPTP. It is technically possible to create a PPTP tunnel connection using MacOS by utilizing some third party software. We decided that the better solution would be to switch to L2TP/IPsec as the security team suggested.
Problem No. 2: Server Bandwidth Overloaded
The Windows Server running the VPN connection was getting overwhelmed by the amount of bandwidth created by all the users. Because the default configuration for a PPTP connection is to tunnel all their traffic through the VPN, everything they accessed was being transported by the server. This means that if a user was watching a Youtube video, streaming Netflix, or doing just about anything that required a lot of bandwidth, all that traffic had to flow from the VPN server to their machine.
Needless to say, when you have 35 users on the same machine this can generate a very large output. At times it was impossible to get anything accomplished because there was too much lag to communicate through Remote Desktop.
Solution: Enable Split Tunneling
Our initial response to the network saturation was to instruct our users to stop streaming videos and other tasks that required a lot of bandwidth while connected to our VPN. We sent an email highlighting all the different activities that required a lot of bandwidth — video streaming, viewing high res photos and downloading large files. We even found a way to monitor who was using the most bandwidth. This can be accomplished through the Remote and Routing Access application on the VPN server.
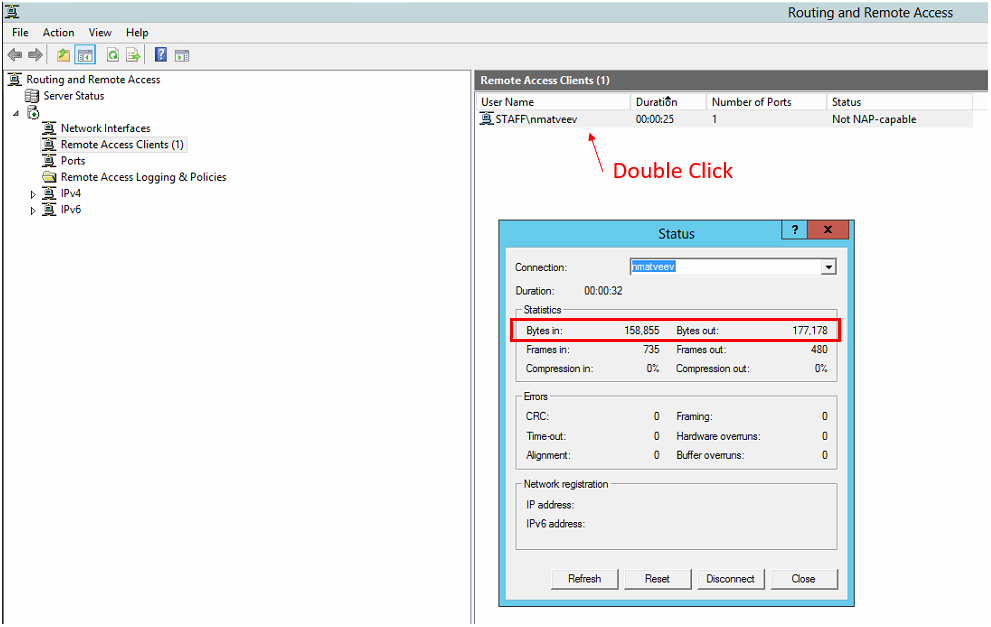
A much cleaner and effective solution was to change the settings on the users' VPN connection to stop tunneling all traffic through the VPN connection. The step-by-step on enabling split tunneling can be found further in this article.
Problem No. 3: Users Not Being Connected to the Internet After Connecting to VPN
Besides the latency we received a lot of reports about unstable connections. The user would connect to the VPN but no data would flow between them and the Server. They would see this on their machine:
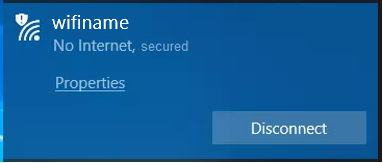
The message was telling them that they had lost connection to the internet. This was a very confusing message since you need an internet connection in order to maintain a VPN connection.
Solution: Check the DHCP IP Ranges for Conflicts
The unstable connections were caused by the influx of new IPs into our DHCP server. We increased our DHCP range in order to facilitate the new IP requirements. What we didn't know is that our DHCP would occasionally hand out IPs that were already registered on another machine. This was because some of our servers had static IPs configured within our DHCP range. Not all of them were reserved which means the DHCP server didn't know that they were in use.
The reason the users would experience a "network outage" when they connected was because their entire tunnel was now sitting on a defunct IP address. No traffic could communicate to or from our VPN server. Because all their traffic was tunneled through the VPN, their computer registered their connection as "No Internet."
Problem No. 4: ISP is blocking VPN Connections
Some of our users could not connect to the VPN even if their operating system allowed it. The IT department would intervene by using the Teamviewer QS application to take control of the machine. For some users, this was due to incorrect configurations. However, this was not always the case. The head of our entire division was able to connect to the VPN during the first week of remote work. After upgrading his ISP he lost the ability to connect despite using the same exact configurations. Hours of troubleshooting produced no results.
Solution: Use the L2TP/IPsec Tunnel Instead of PPTP
The user who could not complete a connection after upgrading their ISP had a similar problem to the MacBook users. Except in this case, it was not the Operating System that was blocking him. It was actually the ISP. They too decided to stop supporting the PPTP tunnel due to the security concerns.
delivered to your inbox.
By submitting this form you agree to receive marketing emails from CBT Nuggets and that you have read, understood and are able to consent to our privacy policy.