What are Transport Layer Protocols?

Quick Definition Transport Layer Protocols, TCP and UDP, are essential for data exchange in networking. TCP guarantees reliable data transmission through retransmission and a three-way handshake, while UDP prioritizes fast data transfer.
Transport layer protocols are crucial components of networking because they provide a way to transmit data packets from one network node to another. Transport protocols serve various purposes, such as streaming video, navigating the internet, and executing transactions. The two core protocols are TCP and UDP.
This article will cover when to use these protocols and the tools needed to diagnose and troubleshoot them. TCP and UDPs fundamental nature mean they are definitely going to show up on any networking certification, such as the Network+ Exam.
What are Transport Layer Protocols?
TCP and UDP protocols are associated with the Transport layer of the OSI model and serve as the fundamental data exchange protocol for the entire internet. In short, transport layer protocols are responsible for ensuring end-to-end communication between devices. They also perform error detection (TCP only), data desegmentation, and data reassembly.
TCP, in particular, is responsible for everything from loading webpages to exchanging data in online gaming. Let’s find out how it does that.
What is Transmission Control Protocol (TCP)?
Transmission Control Protocol (TCP) is a core protocol of the Internet Protocol (IP) suite and is responsible for ensuring reliable, fault-tolerant data is sent from one point to another. TCP takes great strides to ensure all information is transmitted without loss. For example, one feature that sets TCP apart from UDP is the retransmission of lost data. This is done in a particularly clever way.
In the TCP protocol, every packet is given a unique sequence number. The packet sender meticulously keeps track of which packets were sent. In response, the receiving system issues an ACK packet (which stands for 'acknowledgment') that carries the sequence number of the packet it's confirming receipt of. If there's a mismatch in sequence numbers or if one is missing, the sending machine will resend the packet. This continues until a matching ACK confirms successful transmission.
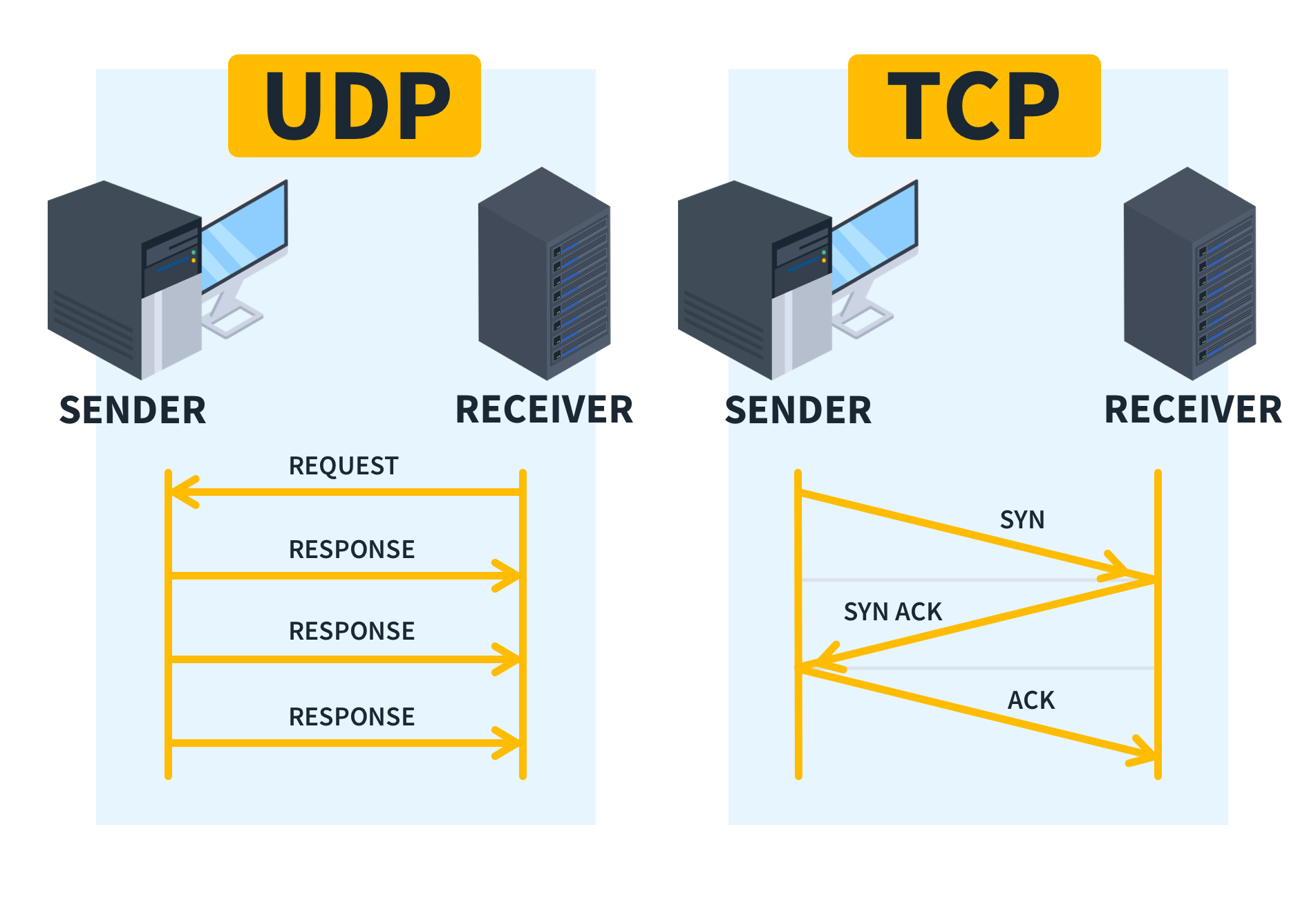
Data retransmission isn’t the only way TCP is reliable. It also uses a three-way handshake to establish durable connections.
In TCP, the three-way handshake is a mechanism of communication to ensure all data is sent and properly received. In a nutshell, this occurs in three parts:
Initialization (SYN): The SYN is an initial packet sent out by a device that would like to establish communication. The packet contains the Synchronize Flag (SYN) and the recipient’s IP Address.
Acknowledge the Initiation (SYN-ACK): Next, the recipient sends back a SYN-ACK packet, assuming it is ready and willing to communicate.
Final Acknowledgement (ACK): Once the sender receives the SYN-ACK, it sends a final ACK to confirm a valid connection.
Once these three “handshakes” are complete, transmission begins. The three-way handshake is often described as TCP’s “connection-oriented” communication hallmark. However, other features such as error detection and flow control also serve as pillars of TCP’s connection-oriented nature.
It would be impossible to name every single use case of TCP due to its ubiquitousness in modern IT communication. However, here are a few use cases to illustrate its usefulness.
Email: All emails are sent using TCP. If it were sent as UDP, the email might arrive with a letter missing here or there, which would seriously hinder communication.
Online Gaming: Currency transactions, login mechanism, and any critical communication necessitates TCP.
Internet Browsing: whether one uses HTTP or HTTPS, the layer 4 protocol is typically TCP. When a user navigates to a web address, TCP is employed. This protocol establishes and maintains a reliable connection between the user's web browser and the web server, ensuring that web pages and associated resources are transmitted accurately and without errors.
While TCP is known for its reliability, it is also known for its latency and high overhead. TCP ensures every packet is sent and accounted for, which may not fit every use case. For example, video streaming does not need every single packet to reach the user — that’s where UDP comes in.
What is User Datagram Protocol (UDP)?
UDP is a connectionless, lightweight counterpart of TCP. Contrary to TCP, UDP’s primary goal is sending datagrams (i.e., packets) as quickly as possible.
One way to think of UDP is a person throwing ping-pong balls into a bucket. The thrower is the sending machine, the ping pong balls are packets, and the bucket is the recipient. It is not important that every single ping-pong ball enters the bucket, just that the majority of them do. The person throwing the balls will naturally miss a few — and that’s OK. This is why UDP is often called “best-effort delivery.”

Best-effort delivery’s best use cases lie in the realm of media transmission. Let’s take a look at a couple of examples:
VoIP calls: VoIP calls are generally made using UDP. That’s why every so often, the picture freezes slightly, a person’s voice skips, or becomes robotic sounding. In voice streaming, it is not important that every single packet arrives perfectly. After all, people are good at picking up on context and don’t need that level of rigor in communication.
Online Gaming: Some aspects of online gaming use UDP as well. Whenever a user moves a character, this is often a UDP connection. Basically, any non-critical data that requires a high response time would be UDP.
DNS: UDP is used for DNS queries and responses. That’s because DNS resolution needs to be snappy and does not require ongoing communication.
How Do You Choose Between TCP and UDP?
There are several factors to consider when deciding which protocol to use. Let’s go over a few of them:
Reliability: TCP provides reliable, audited data and ensures every piece of data is received. If your application requires a high level of fidelity, then TCP is the way to go.
Latency and Speed: UDP is used when it is not important that every single piece of data is received. For example, streaming music might not require every packet. Or if the communication is simply to notify another application to do something else.
Error handling: TCP has built-in error handling that points to the exact issues encountered. Whereas with UDP, the developer will have to develop a custom solution.
In summary, if it is critical that every packet of information is successfully transmitted, then go with TCP. If there is some acceptable level of data loss, then UDP is your best bet. Another critical aspect of choosing protocols is understanding how to effectively scan for them in a network. Let’s cover that next.
What Tools Can Scan Network Ports?
There are numerous tools at the disposal of a trained network engineer; the trick is knowing when and where to use each. Specifically, a network port scanner is a tool that allows you to scan a targeted device and see which ports are open, thus vulnerable. In this section, we’ll walk through a couple of different port scanners that may come in handy, starting with Nmap (Network Mapper).
As a caveat — be careful not to just scan any domain you would like, as this can have possible legal and ethical implications.
Nmap
Nmap is a powerful reconnaissance tool to discover network hosts and services. It is also used as a port scanner by pen testers, system administrators, and security engineers. Nmap uses various techniques to scan ports, such as TCP connection scan, SYN scan, and UDP scanning — all of which we will soon elaborate on.
Netcat
Netcat (also known as nc) is a versatile and well-known network tool that can perform nearly any operation on the TCP/IP suite. Its most notable uses are as a TCP proxy, network daemon testing, port scanning, remote shelling, and much more.
To execute a port scan using nc, type the following command:
nc -zv target_host start_port-end_portThe “z” performs a scan instead of establishing a connection.
The “v” stands for verbose so that we can see the return value.
The target host would be a URL. The start_port is the first port that will be scanned, and the end_port will be the last.
Here is a practical example:
nc -zv www.mywebsite.com 80-100If you are using Mac or Linux, simply open a Terminal and type man nc to learn how to use it on your device. (Or type nc /? on Windows.)
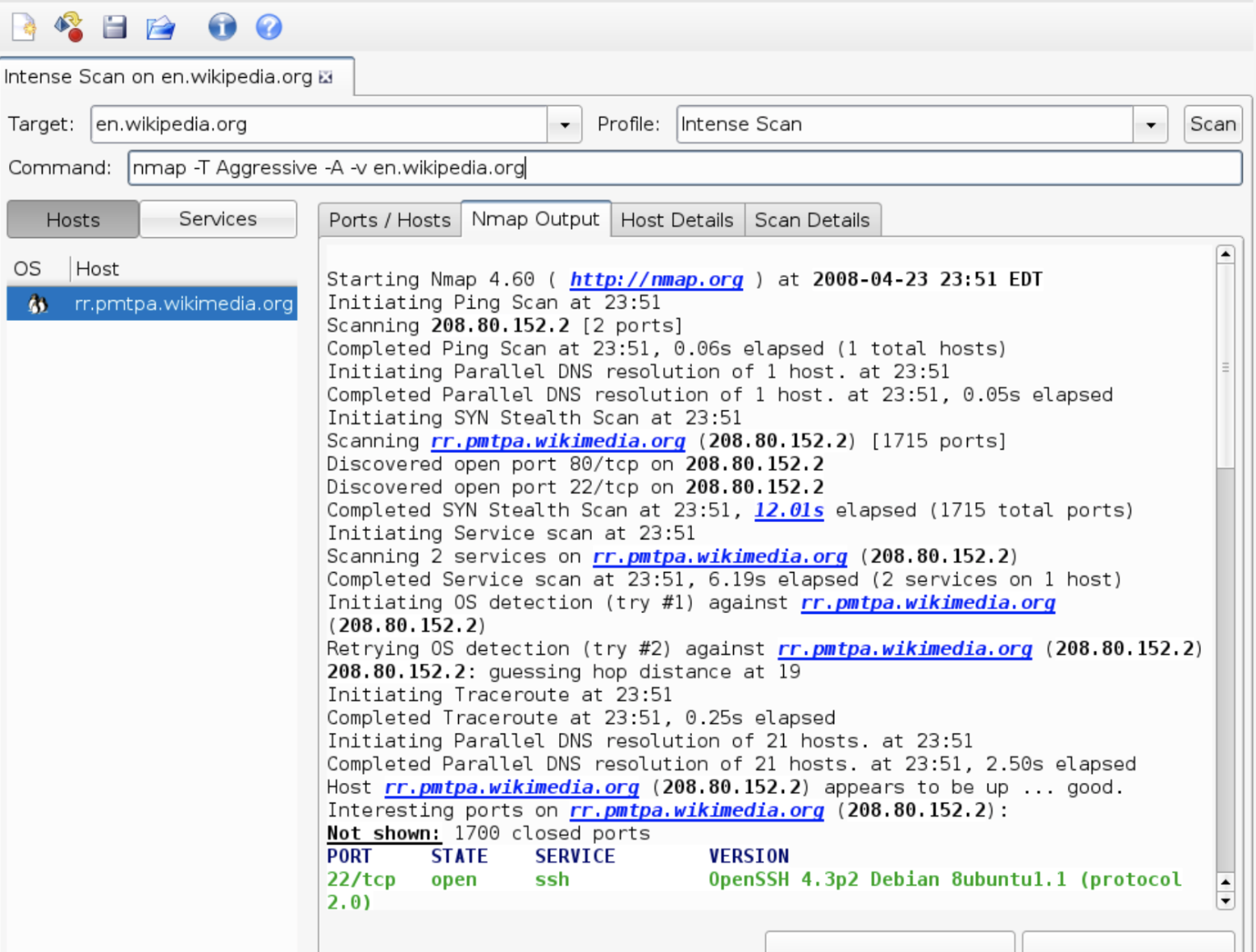
Zenmap
The other examples have been CLI only, but Zenmap provides a GUI for the previously mentioned Nmap. Zenmap provides a more user-friendly and structured approach to utilizing Nmap.
Zenmap’s advantages include allowing you to save an Nmap profile for later, provide deeper result analyses, and use all Nmap features with convenient checkboxes and other user interfaces.
Here is a great visualization of the open-source software from Wikipedia:
Now that we have discussed various tools for scanning networks let’s discuss some techniques leveraged to assess network vulnerabilities.
6 Techniques for Network Port Scanning and Results Interpretation
While the end result of port scanning will be the same, it is important to understand the different techniques used to get there. Like TCP and UDP, different techniques offer trade-offs, such as speed for security. First, let’s take a look at a common technique that nc defaults to —TCP Connection scan.
TCP Connect Scan
This is a common tool used by security engineers to assess the vulnerability of ports on a device. It resolves the three-way handshake, so it generally does not set off intrusion detection alarms. TCP connect scan goes through every port and logs all ports, allowing it to resolve a three-way handshake. However, it is very, very slow.
SYN (Stealth) Scan
SYN Scans, also known as half-port scans, are designed to verify a port's vulnerability faster than a traditional TCP Scan. A SYN Scan waits for acknowledgment from the recipient via the SYN-ACK packet instead of completing the entire handshake.
This makes it significantly faster than a TCP Connect Scan but more vulnerable to intrusion detection systems. Ports that are not open will send an RST signal instead of a SYN-ACK packet.
UDP Scan
Since UDP is not connection-oriented, it is more difficult to determine whether a UDP port is open. UDP scans need to rely on an ACK signal that may not necessarily arrive. However, it is still an important security assessment tool, while still less deterministic than a TCP scan.
Comprehensive Scan Options and Configurations
The amount of scan options that can be applied in Nmap is almost uncountable. Nmap provides plenty of flexibility on how, what, and when you want to scan ports.
However, I’ll list a few scan options to help get you started.
nmap -sS -Pn -sV --version-all -O -p 1-65535 <some-target>-sS: Performs a SYN scan (stealthy).
-Pn: Skips host discovery (assumes the target is up).
-sV --version-all: Tries to identify service versions.
-O: Attempts OS detection.
-p 1-65535: Scans all ports (1 to 65,535).
nmap -p- -T4 -A -v <some-target>-p-: Scans all 65,535 TCP ports.
-T4: Sets the timing template for aggressive (fast) scanning.
-A: Enables OS detection, version detection, script scanning, and traceroute.
-v: Enables verbose output for detailed results.
nmap -p- -sS -sU -T4 -A -v <some-target>-sS: Performs SYN scan (TCP) for port scanning.
-sU: Includes UDP port scanning in addition to TCP.
-T4: Aggressive timing template for faster scanning.
-A: Enables OS detection, version detection, script scanning, and traceroute.
-v: Verbose output for detailed results.
Hopefully, these three configurations will get you started on an exciting port-scanning adventure. Remember, these can also be thrown into a shell script and scheduled using cron to run at regular intervals.
How Do I Interpret Port Scan Results?
Understanding Open, Closed, and Filtered Ports
One thing to remember when analyzing results is that a port should never be open that you do not know about. Only ports with specific purposes should be open for communication. A filtered port is a port that does not respond to a scan at all. This may occur when a firewall is blocking the port, or some other network configuration is preventing a valid response.
Analyzing Potential Security Risks Based on Scan Outcomes
Open and unregulated ports are one of the biggest attack vectors in IT. When analyzing outcomes for security, it is important to determine which ports are open and which services are using that port.
For example, if port 668 is using Telnet and no one knows why, then that’s a serious problem to address. A hacker may be siphoning data on that port via telnet. This is just one example, but it is important to understand and visualize the results to increase and maintain proper security posture.
Wrapping Up
We covered a lot of ground in this article, so thanks for sticking with it. We first reviewed which protocols are used in port-to-port communication: TCP and UDP. Remember, TCP is used for critical data that cannot get lost in transmission. In comparison, UDP is quicker and used for applications that can withstand a certain amount of data loss.
Tools have been developed to monitor these protocols by verifying the ports and services that utilize them. These tools are Netcat, Nmap, and its GUI counterpart, Zenmap.
There are numerous techniques for scanning ports, namely TCP Connection Scan, SYN Scan, and UDP scanning. TCP Connection Scan is slower but more secure. SYN Scan may trigger intrusion detection systems but is faster. UDP scans are often hard to interpret since UDP is not connection-oriented and doesn’t necessarily have to send back a response to the sender.
Understanding these techniques and protocols will make you much more prepared to tackle the Network+ Exam. Once you have a good grasp of IP protocols and port scanning, start understanding the broader topics of network topologies.
Here are a couple of posts to get you started:
Not a CBT Nuggets subscriber? Sign up for a 7-day free trial.
delivered to your inbox.
By submitting this form you agree to receive marketing emails from CBT Nuggets and that you have read, understood and are able to consent to our privacy policy.