Exploring the Metasploit Framework: The Ultimate Penetration Testing Tool

While ethical hacking may seem esoteric, it really is no big secret. All of this stuff can easily be learned with enough practice and diligence. In this article, we'll dive into one of the most useful ethical hacking tools in the industry: Metasploit.
Metasploit has been a cornerstone of the ethical hacking community since 2003, allowing IT security experts to successfully find security exploits. Keep reading to gain a better understanding of this tool through a few real-world examples of Metasploit in action.
What is the Metasploit Framework?
Metasploit is an open-source penetration testing tool written in Ruby. Penetration testing entails probing an IT system for any possible means of entry, and can be done in several ways: through a phishing attempt, by cracking a password, or by exploiting a firewall misconfiguration. And ethical hackers worldwide use the Metasploit framework to find vulnerabilities in systems so they can eliminate and prevent them from occurring again with bad actors.
Because Metasploit is open-source, it can easily be found on GitHub. It’s also pre-installed onto Kali Linux. Another great thing about Metasploit is that it contains a public database of known vulnerabilities and exploits. Once you find a vulnerability with a web application, it’s immediately documented in the database. This will not only strengthen your own security posture but the security posture of others as well.
Now that you have a good understanding of what Metasploit actually is, let’s talk about what can actually be done with this powerful framework.
Exploitation Techniques with Metasploit Framework
Metasploit will give you the ability to control another computer from the comfort of your own desk. While the steps to do so are relatively complex, it is certainly not out of the realm of possibility to obtain root access to another's computer. Root access means having access to everything on the computer.
Essentially, the only thing you need to know to kick off the process is the IP address of the computer that needs to be broken into. Then, once access has been obtained, the IT security professional can run the command get system within the Metasploit CLI, and gain root access.
A hacker often will use commands such as psexec to gain access to the host’s terminal to retrieve files, plant viruses, delete data, or any number of things.
Scan a System for Security Vulnerabilities
Metasploit isn’t only for hacking into a system. It can also scan a system for potential exploits. An ethical hacker doesn’t have to guess and check every exploit that exists. Instead, they can focus on searching for vulnerabilities that have already been found during the scan.
Generally, the commands used to execute the scan will look like this: nmap -sC <ip-address>. The IP address will be the address of the target you are trying to penetrate.
While Nmap (network mapper) has been around for longer than Metasploit, it is usually integrated into the framework because of its ease of use. This is not the only way to scan, however, there are plenty of other scripts that one can use to refine the vulnerability scan.
Once this information is successfully obtained, it becomes far easier to exploit the vulnerability — and inform your organization or client of the problem.
Advanced Features of Metasploit Framework
Clearly, Metapsloit has a wealth of scripts and tools needed to gain entry into a system. However, in the real world, successful penetrations are often accomplished via social engineering. Social engineering refers to the psychological manipulation of others to gain access to an otherwise secure system.
One of the most common methods of social engineering is phishing, which consists of sending messages (most commonly emails) that pretend to be from a reputable source in order to get recipients to reveal personal and sensitive information like passwords or credit card numbers.
Metasploit enables users to create a phishing campaign to evaluate the readiness of an organization. The image below provides a closer look at the Metasploit user interface for phishing campaigns.
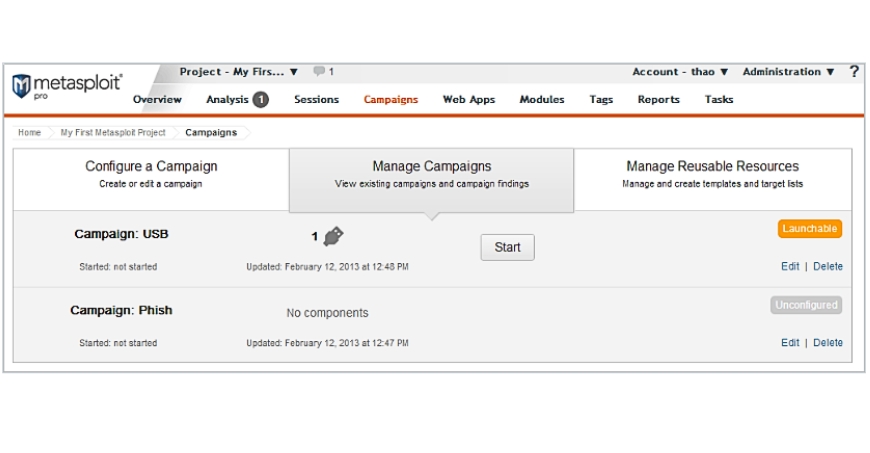
Once you have the campaign created, Metasploit will give you the option to do the following:
Create a fake email to test the recipients.
Collect data on how many people clicked on a malicious link.
Embed viruses and other malicious software into the emails.
All of this (and way more) can be done from a straightforward UI. No command line is involved.
Final Thoughts on Metasploit Framework
Now that you know more about Metasploit, it's easy to see why it's such a popular tool among ethical hackers. Its advanced capabilities include the ability to create phishing campaigns, gain entry into systems, and scan thoroughly for vulnerabilities.
Lastly, Metasploit keeps a meticulous record of all exploits that have been discovered. This makes it easy to track and catalog different vulnerabilities that could infect your system. Metasploit brings a lot to the table — and any ethical hacker would be remiss to overlook its potential.
Not a CBT Nuggets subscriber? Sign up for a 7-day free trial for a commitment-free week of IT learning. There's plenty of cybersecurity training to help you learn the skills needed to help you keep networks and data safe.
delivered to your inbox.
By submitting this form you agree to receive marketing emails from CBT Nuggets and that you have read, understood and are able to consent to our privacy policy.