How to Troubleshoot a Failed Ping Request

Network connectivity is the backbone of every IT environment, and when a simple ping fails, everything grinds to a halt. Whether you’re validating a new firewall deployment or trying to track down a stubborn outage, ping is still one of the fastest ways to spot where traffic is breaking.
But ping isn’t magic. If a device refuses to respond, you could be dealing with anything from a misconfigured interface to an intentional ICMP block. And on Palo Alto Networks firewalls, that behavior is often by design.
In this guide, we’ll cover general steps for handling failed ping tests and then dive into how Palo Alto firewalls process ping requests and how to troubleshoot failed pings step-by-step using modern tools and best practices.
How to Troubleshoot Network Issues
Every network breaks eventually—cables get bumped, routes disappear, firewalls drop packets, and users swear they “didn’t change anything.” When connectivity fails, a structured approach can save you hours of guesswork.
When it comes to troubleshooting network issues, the workflow usually looks something like this:
Check the Physical Layer First
Before diving into configs, make sure nothing obvious is broken. Loose cables, dead switch ports, disabled interfaces, or an unplugged firewall can look a lot like complex routing problems. Power-cycle gear if needed, verify link lights, and make sure the right devices are actually connected to the right networks.
Validate IP Addressing and DNS
Once the hardware checks out, confirm that the device has the correct IP address, subnet mask, gateway, and DNS settings. Address conflicts or expired DHCP leases are still some of the most common causes of random network failures. Tools to use: ipconfig or ifconfig to view local addressing; nslookup to verify name resolution; Test-NetConnection (PowerShell) for modern reachability testing.
Use Basic Connectivity Tests: Ping and Traceroute
Ping helps you confirm whether a host is reachable and how long it takes to respond. Traceroute (tracert on Windows) shows where packets are dropping along the path. If ping works but applications don’t, you’re likely dealing with a port, protocol, or firewall issue. If traceroute dies at a specific hop, you’ve found your probable choke point.
Look at Active Connections and Traffic Flow
If things still look fuzzy, check what the device is actually doing. netstat shows active sessions and listening ports. route print (Windows) or ip route (Linux) shows which gateway traffic is using. Packet captures can reveal whether traffic is leaving the interface and how the remote device responds. Together, these tools help you isolate whether the issue lives on the endpoint, the network, or somewhere in between.
How to Troubleshoot a Ping Request
One of the most fundamental tasks that every network engineer or network technician must perform is the troubleshooting of ping requests in Palo Alto firewalls. ICMP and ping messages may be used against us for network discovery or to attack our systems; hence, they are disabled by default.
So on its data plane interfaces, the Palo Alto firewall’s default attitude is that if someone sends a ping, it won’t react. Let's walk through where we’d go in the Palo Alto firewall to set or adjust that behavior. Even with a Management Profile enabled, ICMP may still be dropped by Zone Protection or DoS Protection profiles, depending on your configuration.
The data plane interfaces ethernet1/1 and 1/3 in the following configuration are both not receiving ping requests. They also refuse to accept or enable others to communicate with them to manage the box.
For the time being, the only way to administer this Palo Alto firewall is through the management interface, which does accept pings. By default, it only allows HTTPS and SSH sessions on the administration interface.
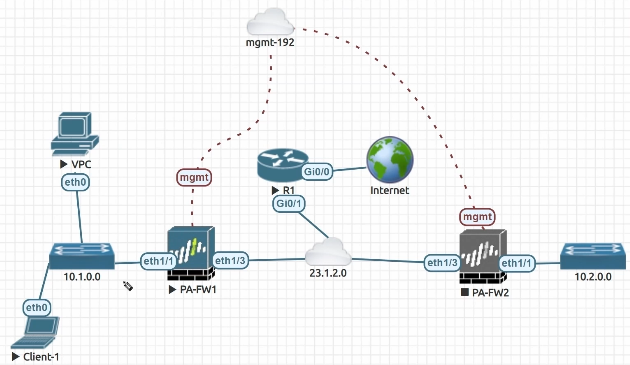
Figure: A Network Topology for Troubleshooting Ping
Troubleshooting Ping on Palo Alto Firewalls
Once the basic network checks are out of the way, the next step is understanding how your firewall handles ICMP. On Palo Alto Networks firewalls, this matters even more because ping is intentionally disabled on data plane interfaces unless you configure otherwise. Here’s how to troubleshoot failed ping requests specifically on Palo Alto firewalls.
Verify the Interface Configuration
Start in the Network tab and open the Interfaces section. Identify the interface you want to test, such as ethernet1/1 for an internal network or ethernet1/3 for an external network. If the interface doesn’t respond to a ping, it's likely not associated with a Management Profile that allows ICMP.
Create or Update a Management Profile
Palo Alto firewalls control administrative access through Management Profiles. Without one, an interface won’t accept ping, SSH, HTTPS, or other management services. To enable ping, create a profile with ICMP allowed.
Navigate to Network, then Interface Mgmt, and add a new profile. Give it a descriptive name and select Ping under Network Services. You can also enable HTTPS or SSH if you want to manage the firewall from that interface, but avoid enabling insecure options like HTTP or Telnet.
Apply the Profile to the Interface
Return to the interface you’re troubleshooting and assign the new Management Profile to it. Once the profile is attached, commit the configuration so the change moves from the candidate configuration to the running configuration. After the commit finishes, the interface will begin responding to ping.
Test the Ping from a Client
Use a client on the connected network to send a ping to the interface address. If everything is configured correctly, the ping should succeed. If it still fails, check for additional controls such as Zone Protection profiles, DoS protections, or routing issues that might be filtering ICMP traffic upstream.
Wrapping Up
Even in well-designed networks, connectivity issues can pop up without warning. A new device, a misapplied policy, or an unexpected interaction between systems can break something as simple as a ping test. Palo Alto firewalls add another layer of complexity because data plane interfaces don’t respond to ICMP unless you explicitly allow it.
Modern PAN-OS versions use Management Profiles to control which services an interface will accept. Once you create a profile that permits ping and apply it to the appropriate interface, you can quickly verify reachability and continue troubleshooting from there. If pings still fail, expand your checks to include routing, security policies, and any zone protection settings that may be filtering ICMP traffic.
With a structured workflow and a clear understanding of how Palo Alto firewalls handle management traffic, you’ll be able to isolate issues faster and keep your network running smoothly.
Want to learn more? Check out our Advanced Network Understanding with Wireshark Online Training.
delivered to your inbox.
By submitting this form you agree to receive marketing emails from CBT Nuggets and that you have read, understood and are able to consent to our privacy policy.