What is Port 23?
by Colin Cohen | Published on October 20, 2023

Port 23 is the default TCP port for Telnet, which allows you to connect to other devices remotely. Due to its lack of security, Telnet’s use has largely been superseded by SSH.
What is Port 23?
Port 23 is the default Telnet port, and it is used for remote terminal emulation of both computers and devices.
What is the Telnet Protocol?
The Telnet protocol lets a client device connect to a Telnet server over port 23. After authenticating on the server device, the client can then run commands on it.
What is Remote Terminal Emulation?
You can’t always physically be at the device you need to operate, so software like Telnet lets you remotely connect to it and access it through a remote terminal or shell. This, in turn, allows you to run commands on it as if you were physically at it.
Port 23 For Switches, Routers, and NAS
Remote terminals are not just for computers. Using software like Telnet, you can connect to switches, routers, network-attached storage (NAS), and just about any networked device with a modern operating system such as Linux installed on it.
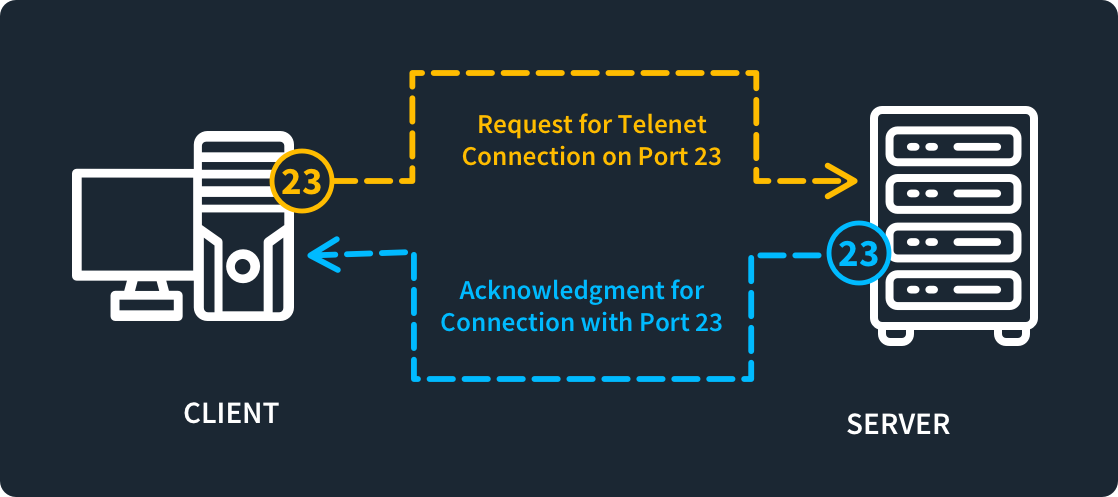
What is Telnet Port 23 Used For?
Telnet on port 23 lets you issue commands on a remote device. You will use it mostly on legacy systems and isolated networks.
RELATED: The 12 Most Important Protocols to Learn for Networking
How Port 23 Telnet Works
Most Unix-like operating systems include a Telnet client. To access it, run the following command from a terminal:
telnet [host] [port]
The [host] is either the hostname of the device or its IP address.
You can also specify the [port] that you want to communicate over. If you don’t, Telnet will use port 23 by default. Note: some system administrators use Telnet on other ports for debugging network services, making it easy to issue commands and view their responses.
After connecting to the host, you can log into it as if you were on the device directly.
In Windows, you need to enable Telnet as a Windows feature in your control panel.
Port 23 Telnet Provides Command Line Access
After you connect to a Telnet server and perform any required authentication on the device, you have the same command-line access that you have on your computer. Depending on the permissions of the user that you are logged onto, you can view, create, edit, and delete files and folders, and you can run programs that exist on the server.
Why Do Legacy Systems and Isolated Networks Use Port 23?
Today, Telnet has limited use because of its lack of security. But this is not a big issue for many legacy systems and local area networks (LANs) that are disconnected from the Internet. On some legacy systems, you may actually have to use Telnet because they don’t support more modern protocols.
Is Telnet Still Used?
Telnet is still used, but because it is inherently insecure, it is often blocked. For the most part, Telnet use has been replaced by Secure Shell (SSH) protocol.
Telnet is Inherently Insecure
Due to Telnet not performing any encryption when it communicates over port 23, it is inherently insecure. Attackers could view credentials or other sensitive information passed during a Telnet session through various mechanisms, such as packet sniffing. For this reason, many believe that Telnet should never be used over the Internet.
Should Port 23 Telnet Be Blocked?
Many organizations always block port 23 in their firewalls. This is because of Telnet’s lack of security and because attackers will often specifically target port 23. Fortunately, blocking port 23 in their firewall isn’t an issue for most of these organizations, as anything you can do in Telnet you can also do in SSH, which provides shell access securely.
The Security Vulnerabilities of Port 23 Telnet
Port 23 is highly vulnerable because it transmits data in the clear and has little to no authentication.
Telnet Port 23 Transmits in the Clear
Telnet transmits in clear text over port 23, making it vulnerable to man-in-the-middle attacks. Anyone who can analyze packets sent over the network as it passes over routers, switches, hubs, and other devices can view whatever a Telnet user types within a session.
Little to No Authentication with Port 23
Telnet implementations often lack inherent authentication, and the authentication mechanisms available are also often vulnerable.
It is not uncommon for devices with Telnet enabled to provide unrestricted access.
Why Does Port Scanning Frequently Targets Port TCP Port 23?
As Telnet is so insecure, it is a frequent target of attackers, who use port scanners and other tools to find computers in which port 23 is open.
Port 23 on TCP
Because of how Telnet operates, you use TCP as a transport protocol when using port 23.
Why Telnet Port 23 Uses TCP
Telnet uses TCP for its communications over port 23. It does this because TCP offers connection-based delivery of data. TCP also guarantees this delivery, which means that Telnet does not need to perform any confirmation of data delivery within its protocol.
What are Potential Port Conflicts With Port 23?
There are potential conflicts when using port 23, as some devices won’t allow it, and you can’t run services simultaneously.
Some Devices Don’t Allow TCP Port 23
Many devices will block port 23 by default because of the insecure nature of Telnet. In these cases, you will have to use port forwarding to a port such as 2323 to enable Telnet.
You Can’t Run Simultaneous Port 23 Services
At times, you may run into the issue of not being able to bind port 23 to your Telnet server. This is likely because it has already been bound to another server. To discover what application is bound port 23, you can run the following command from your terminal:
netstat -aon
The output of this command will indicate the process bound to port 23, which you will need to stop before you can start your Telnet server.
Key Takeaways about Port 23
Telnet may have limited purpose in the modern world due to security concerns, you still may use it to remotely connect to legacy systems over port 23. Port 23 may also be used in situations where security is not a concern, such as on a Local Access Network (LAN). That said, there are serious cybersecurity issues with port 23. When possible, opt for the SSH or implement other security measures to ensure communication is secure.