Top 3 Cybersecurity Threats and How to Prevent Them

Cyberattacks occur constantly, and it can feel like it's only a matter of time before a cybersecurity breach strikes your organization. There's a good reason for that. According to the TRC Annual Data Breach Report, there's been a 72% increase in total compromises from 2021 to today.
While a cybersecurity breach may seem inevitable, there are steps that can be taken to greatly reduce threats. The first part of cybersecurity is understanding the many possible vectors of attack a hacker can take.
In this post, we'll discuss three different security breaches, their definitions, and best practices for preventing them. Let's start with the most common and least technological threat: social engineering.
What is Social Engineering, and How Does it Work?
Social engineering is a broad term that can be used to describe numerous different scams and hacks. It involves deceiving members of an organization into revealing sensitive information or granting unauthorized access, often by impersonating trusted individuals or creating a sense of urgency.
One of the most common social engineering methods is phishing. Another example is impersonation, where a hacker claims to be an employee to obtain information. Let's first examine phishing.
What is Phishing?
Phishing is when a hacker sends an email that appears legitimate but is not. The email is the bait, the hacker is the fisherman, and you are the fish. A phishing attack aims to obtain data by claiming to be a person or organization of authority. Phishing emails appeal to the user's sense of urgency or some other psychological aspect that would get someone to click the link. Let's look at a quick example.
Let's say you received an email from the "Human Resources Department." The email says that your badge will expire tomorrow, and you must click the link to reserve a badge replacement time. If you do not reserve a spot, your badge will expire, and you will no longer be able to access your workplace.
This email appeals to our sense of urgency. We don't want to be unable to access our workplace. It also appeals to our sense of authority—i.e., our HR department is a legitimate source.
Unfortunately, if you click the link, you will be forwarded to a fake website asking you to enter your email and password to reserve a badge replacement time. Now, the hacker has your username and password and can do unprecedented damage to you and your organization.
Now that we understand how phishing works, let's explore ways to prevent it
How to Prevent a Phishing Attack
The best way to prevent a phishing attack is to look for red flags. One option is to make sure all emails coming from outside your organization are put into a separate folder. Make sure the from and reply-to addresses are the same and from your organization. If you’re not sure, it’s best to ask IT directly.
Next, advise your IT staff to set up phishing email training to send to employees so they can practice what to look for when phishing attempts occur. Often, phishing emails have misspelled words or strange wording, as if the person who wrote them doesn't speak English.
Phishing attempts always appeal to employees' sense of urgency to get them to click the link. For example, they might say something like, "You will no longer be able to work here if you don't update your address on this link." Remember: Stop and think before clicking that link.
What is Impersonation?
The next form of social engineering is impersonation. A hacker will claim to be an employee of the organization and try to get their password reset. The hacker will often trawl logs that leak onto the website.
They can use this to obtain information they wouldn't otherwise have. Then, they call the IT department and give information that will seem credible, such as employee numbers, date of birth, and other information.
How can Impersonation Attacks be Prevented?
Well-trained employees who vigorously follow procedural compliance can prevent impersonation attacks. For example, check the phone number the call is coming from. If it is not a recognized number, that is a red flag. Ask the "employee" who their manager and co-workers are. Ask them a little bit about their job. If they fumble, then that is a bad sign.
It is human nature to be as helpful and assistive as possible when talking to people; this is a crucial mistake when dealing with IT security. If you are suspicious, ask follow-up questions or simply hang up the phone and inform your manager of a potential cybersecurity attack.
Impersonation is one of the more insidious aspects of cybersecurity because it is so personal. Next, let's talk about how ransomware can cripple your organization and what steps can be taken to prevent it.
What is Ransomware?
Ransomware is a type of virus that threatens to publish private data or withhold critical data hostage until a certain demand is met. Typically, the demand is monetary compensation in the form of cryptocurrency.
It is a sad reality that ransomware attacks are becoming commonplace. In 2023, there were more than 317 million ransomware attempts worldwide targeting a wide range of organizations, including the Royal Mail in the UK, Aloha POS, and the city of Dallas. More often than not, organizations have to pay the criminals the ransom to get their data back—and some are never able to retrieve their data, even after paying.
Protecting against a ransomware attack after it has already occurred is sort of like locking the barn door after the horses ran away. Once the hackers have your data, they have your data. However, numerous steps can be taken to harden your security infrastructure to prevent these travesties from occurring.
Endpoint Hardening Can Prevent Against Ransomware
One of the best ways to prevent ransomware is to ensure your software engineers are taking a proactive approach to security when designing a system. This is called Security by Design.
One such method of preventing ransomware is to harden your endpoints. Think of an endpoint as an access point to your application. Whether it is via a login screen or a URL for a REST endpoint, make sure that all data is sanitized so that hackers cannot send malicious data to the endpoints. This is often referred to as SQL injection or Cross-Site Request Forgery.
Another good way to harden your endpoint is to disable Cross-origin Resource Sharing (CORS). This will ensure that your app only communicates with an authenticated server. Please note, though, that there are some instances in which we want CORS enabled. For example, Google Fonts require CORS.
Lastly, two-factor authentication should be enabled on all devices. This will make it much more difficult for a hacker to steal somebody’s device and crack the password.
Keeping Software Up to Date to Prevent Ransomware Attacks
Another important strategy to prevent ransomware is to keep all software and frameworks up to date. For example, if your team uses Spring Boot for their Java framework, make sure it is on the latest version. That goes for all other frameworks, such as React and Angular.
The organizations responsible for maintaining these frameworks constantly find security vulnerabilities in their code and update them accordingly. If you do not update the code, it is only a matter of time before a hacker exploits it.
While many hackers utilize proactive approaches such as social engineering and ransomware, often, all they have to do is wait for a vulnerable security misconfiguration. Let's walk through that because it is becoming such a serious issue.
Beware of Cloud Security Misconfiguration
Every cloud hack has been traced back to a misconfiguration. Google, AWS, and Microsoft go to great lengths to ensure the security of their data storage tools.
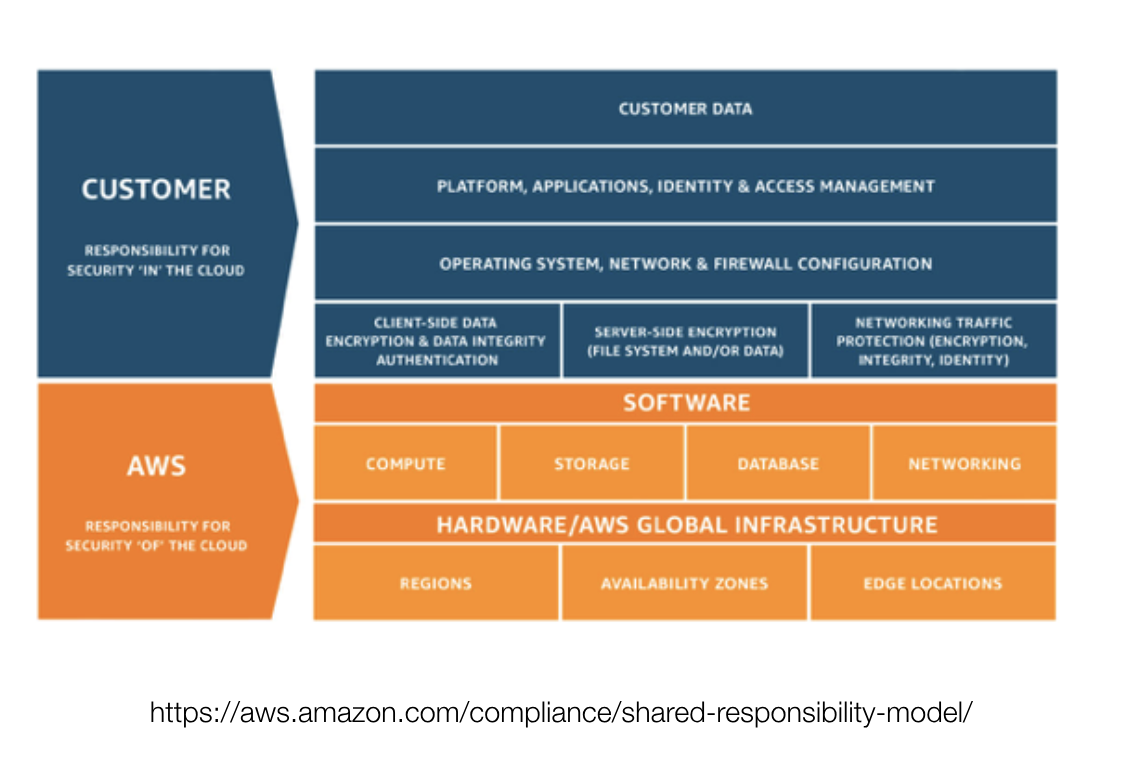
In the cloud world, however, there is a shared responsibility model that determines the duty of the cloud provider and the responsibility of the user. Each cloud provider has some version of the model, but the AWS version looks like this:
Notice that the customer is responsible for a wide range of duties, ranging from their data to access and management to firewall configuration. These are where hacks most often occur. Let's talk specifically about S3 buckets, AWS's flagship data storage model.
What is an S3 Bucket, and Why is it a Cybersecurity Threat?
For the uninitiated, an S3 bucket is a scalable document-based database. It can store any data imaginable and is completely scalable to meet your needs. The bucket is accessible via endpoints or a user interface on the AWS console.
In June 2017, a hacker revealed 198 million voter records from a misconfigured S3 bucket. Suffice it to say, that is not good. The problem can be traced back to an S3 bucket being misconfigured for public accessibility. If that is not a wake-up call to cybersecurity experts, I don't know what is!
S3 buckets are created secure by default and do not have access to the Internet. However, configuring S3 endpoints and determining which ones should have access to the internet can be challenging. This process is rife with misconfiguration, and AWS engineers often accidentally give an S3 bucket access to the Internet.
Once an S3 bucket has this access, any hacker can hit that endpoint and retrieve huge amounts of data. For example, Grayhat Warfare can be used to find public S3 buckets. Then, they can ransom it back to the organization, sell it to a third party, or blackmail somebody.
How to Prevent Misconfiguration of S3 Buckets
The easiest way to eliminate this threat is to be very careful when configuring the S3 buckets. Have more than one person verify the configurations before releasing them into the wild.
Only allow users who are certified in the technology access to the cloud console. Test engineers can also create integration tests that ping the bucket to verify it does not have access to the internet. If it does, the test fails, and the software engineering department is notified.
This is not exclusive to Amazon buckets. Azure and Google buckets can potentially be misconfigured in the same way.
Final Thoughts
In this post, we discussed three major vectors of attack: social engineering, ransomware, and cloud security misconfiguration. Each is very different and diverse, and each involves different employees in the organization. Social engineering works by tricking people, ransomware exploits security bugs, and cloud security hacks exploit configuration errors.
It is important to remember that cybersecurity is not relegated to one particular team. It is everyone's responsibility. Everyone, from the CEO down, should have some level of cybersecurity awareness training.
Not a CBT Nuggets subscriber? Sign up for a free, 7-day trial.
delivered to your inbox.
By submitting this form you agree to receive marketing emails from CBT Nuggets and that you have read, understood and are able to consent to our privacy policy.